Live Patching on SLES 12
On SLES 12 systems, live patching is managed by kGraft. For in depth information covering kGraft use, see https://documentation.suse.com/sles/12-SP5/html/SLES-all/cha-kgraft.html.
Before you begin, ensure:
-
Uyuni is fully updated.
-
You have one or more Salt clients running SLES 12 (SP1 or later).
-
Your SLES 12 Salt clients are registered with Uyuni.
-
You have access to the SLES 12 channels appropriate for your architecture, including the live patching child channel (or channels).
-
The clients are fully synchronized.
-
Assign the clients to the cloned channels prepared for live patching. For more information on preparation, see Set up Channels for Live Patching.
-
Select the client you want to manage with Live Patching from , and on the system details page navigate to the tab. Search for the
kgraftpackage, and install it.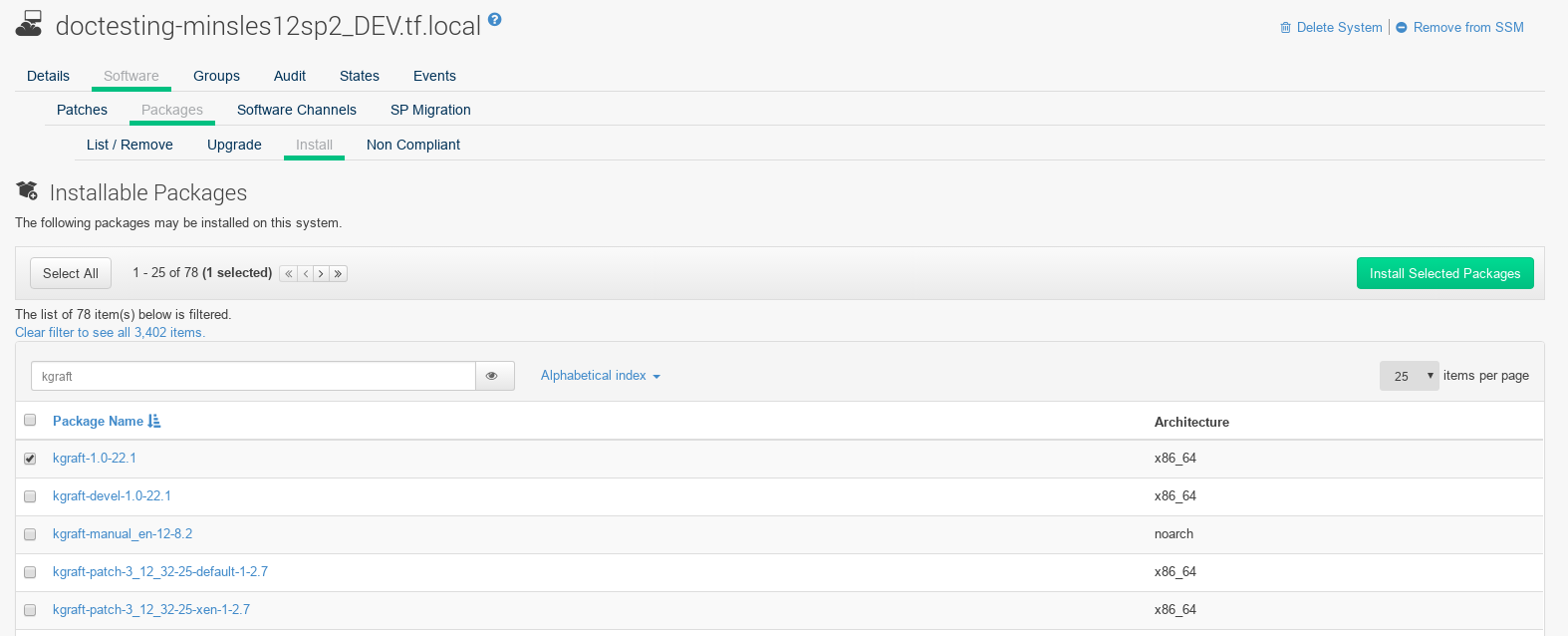
-
Apply the highstate to enable Live Patching, and reboot the client.
-
Repeat for each client that you want to manage with Live Patching.
-
To check that live patching has been enabled correctly, select the client from , and ensure that
Live Patchingappears in theKernelfield.
-
In the Uyuni Web UI, select the client from . A banner at the top of the screen shows the number of critical and non-critical packages available for the client.
-
Click Critical to see a list of the available critical patches.
-
Select any patch with a synopsis reading
Important: Security update for the Linux kernel. Security bugs also include their CVE number, where applicable. -
OPTIONAL: If you know the CVE number of a patch you want to apply, you can search for it in , and apply the patch to any clients that require it.
|